End-to-end security
The security systems implemented by XOne make the whole system and processes more effective and efficient.
In addition, they guarantee that the company knows the types of risks it faces and that they provide enough information to enable them to make the best decisions to face the possible challenges in terms of security.
XOne incorporates predictive and prescriptive analysis.
The security of the platform and all its apps is prioritized, providing total security throughout the process, as well as the transfer of secure information.
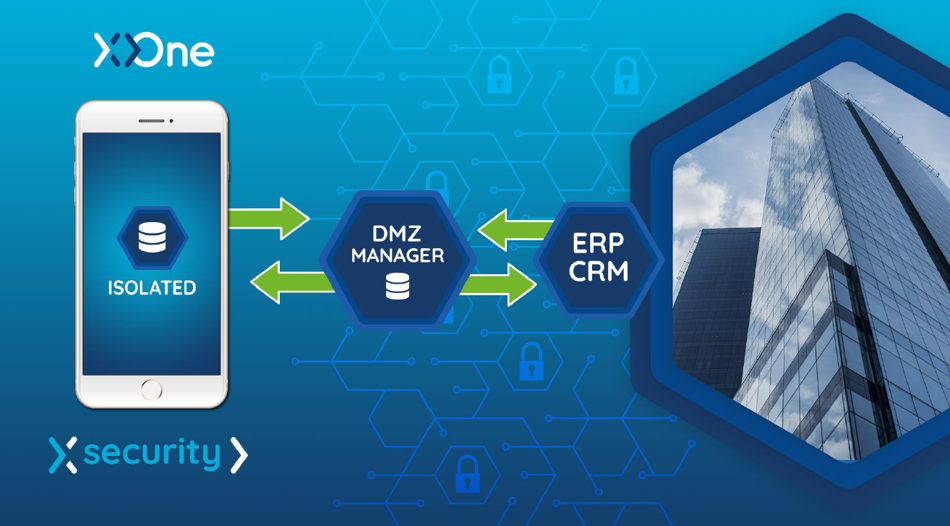
The Security Broker DMZ powered byXOne is a web attack protection system, where you get a separation of all communications between the central and the devices.
The system is ready to put as many brokers as deemed necessary.
The objectives of the XOne Broker are:
Avoid identity theft
Avoid attacks due to denial of service
WEB communications are only enabled under the SSL protocol, so that these communications are already encrypted on that SSL.
The communications used in this environment, even with that intermediate broker, are quite agile, and improve performance.
IDS Core
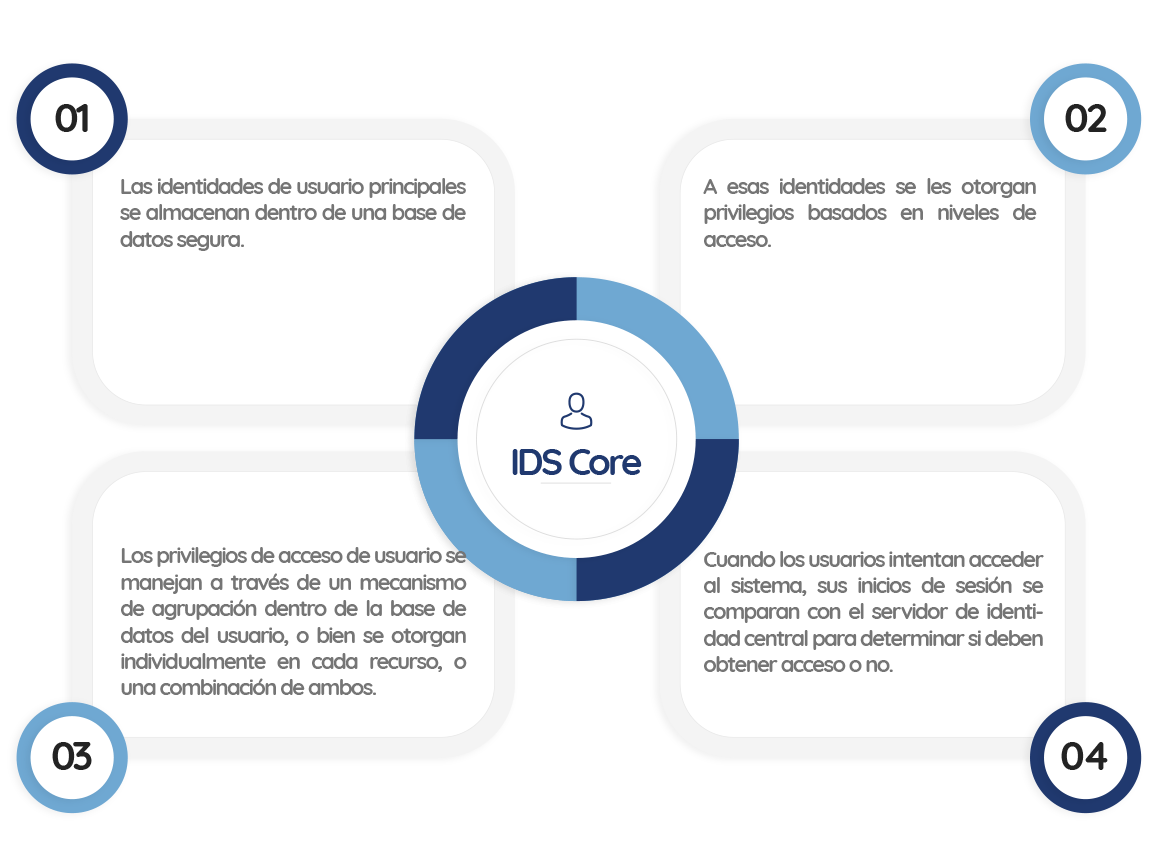
IDS Core is the core of any infrastructure for access and identity control. It allows identifying the user and managing which resources can be accessed.
It provides a stable identity for users in all applications of our system.
Total interconnectivity
XOne offers a very complete IDS Core solution to manage identities through different platforms, systems and services.
It is a system that is responsible for authenticating, authorizing and securing both the apps and users in our developments.
IDS Core is able to connect and manage a multitude of identities between different applications, APIs, clouds, mobile devices, IoT …
It is responsible for implementing common protocols, keep the apps safe and follow the standards in terms of security and control, so that the usability of our apps is not affected.
Secure your apps with IDS Core
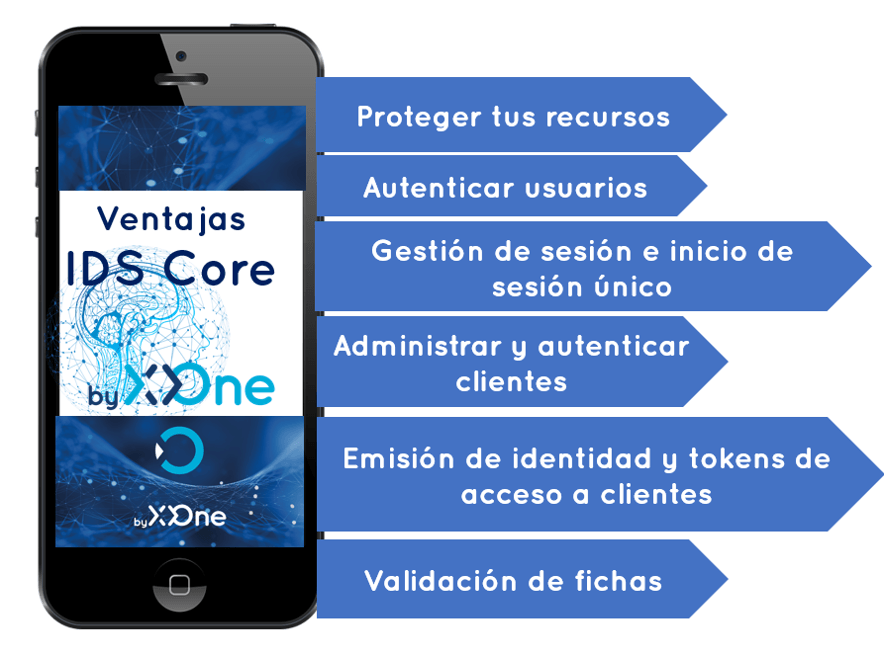
Outsourcing the fundamental security functions to a security token service avoids duplication of functionality in apps and endpoints.

Authentication
Authentication is necessary when an app needs to know the identity of the current user. Usually, these apps manage the data on behalf of that user and must ensure that this user can only access the data for which it is authorized.
The most common authentication protocols are SAML2p, WS-Federation and OpenID Connect.

API access
The apps have two main ways with which they communicate with the APIs: using the identity of the app, or delegate the identity of the user. Sometimes, both methods are combined.